As part of my Azure feature series lets take a look at Bastion (now in preview)
What is it?
Securing access to public facing cloud based VMs is a potentially risky and costly concern for businesses. Using services like JiT (Just in Time Access) to reduce the attack surface requires that your Security Center Service Plan has been upgraded to Standard as the service is not available on the Basic Service Plan.
Say hello to Azure Bastion
Now with Bastion you can remove the attack surface completely by allowing connections via port 443 for Windows and SSH for Linux integrated into the Azure Portal, thereby removing the risk of port scanning and removing the need for public facing IP addresses for your VMs.
Below are some of the key features currently available at this time:


How to activate the Public Preview
The service is currently in preview, which means you need to activate it with the below steps:
- Make sure you are connected to the Azure Preview portal here
- Open Azure Shell and run the below three commands:
(If you have the Az PowerShell module remember to change AzureRM to Az)- Register-AzureRmProviderFeature -FeatureName AllowBastionHost -ProviderNamespace Microsoft.Network
- Register-AzureRmResourceProvider -ProviderNamespace Microsoft.Network
- Get-AzureRmProviderFeature -ProviderNamespace Microsoft.Network
Getting started
From the homepage of the Azure Preview Portal click + Create a resource and search for Bastion (Preview), then click create.
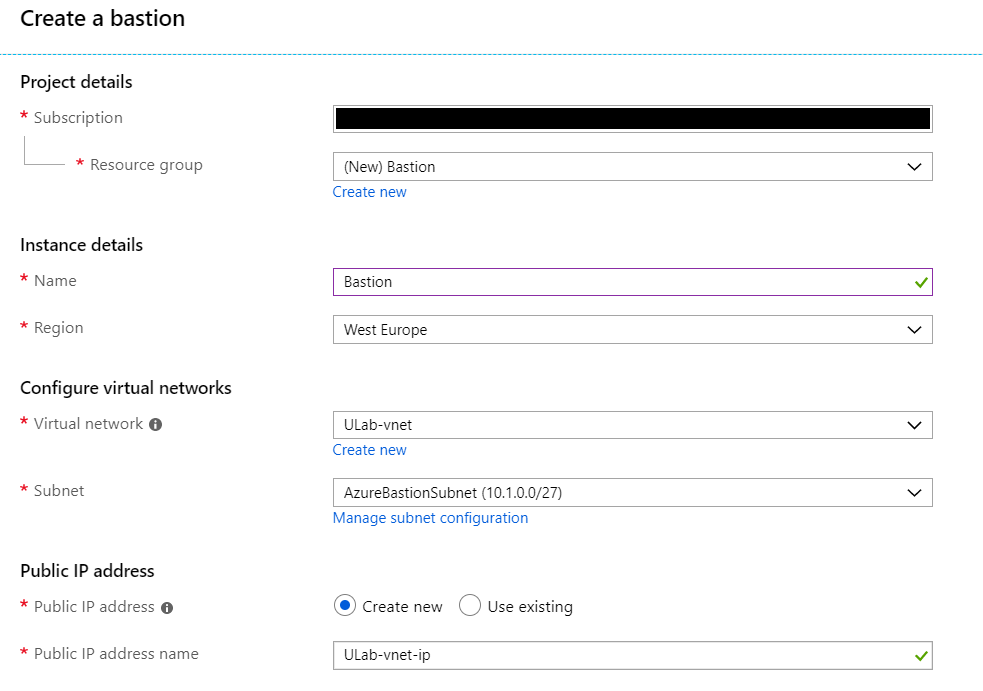
Choose your subscription and resource group, it is important to note that you have to create a subnet called AzureBastionSubnet. This value lets Azure know which subnet to deploy the Bastion resources to. It is recommend to use at least a /27 or larger subnet. Create the AzureBastionSubnet without any Network Security Groups, route tables, or delegations. Once done create the Bastion.
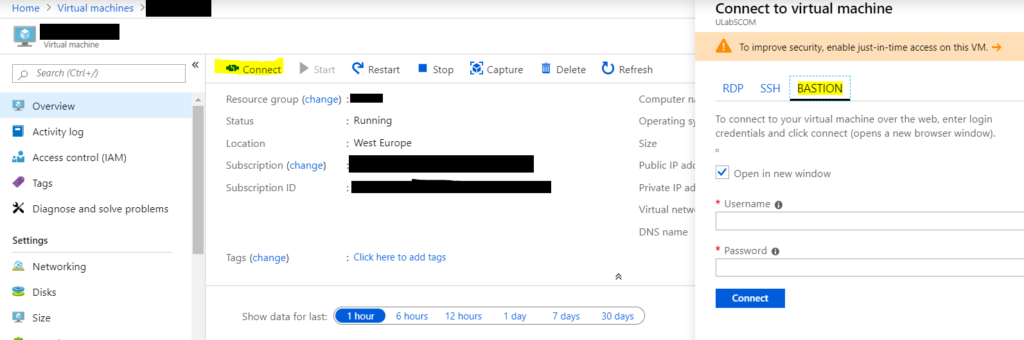
Once your Bastion is deployed, from the Azure Portal navigate to the VM you want to connect to and click connect, you will see a new option called BASTION next to the familiar RDP and SSH options. Enter the credentials and click Connect.
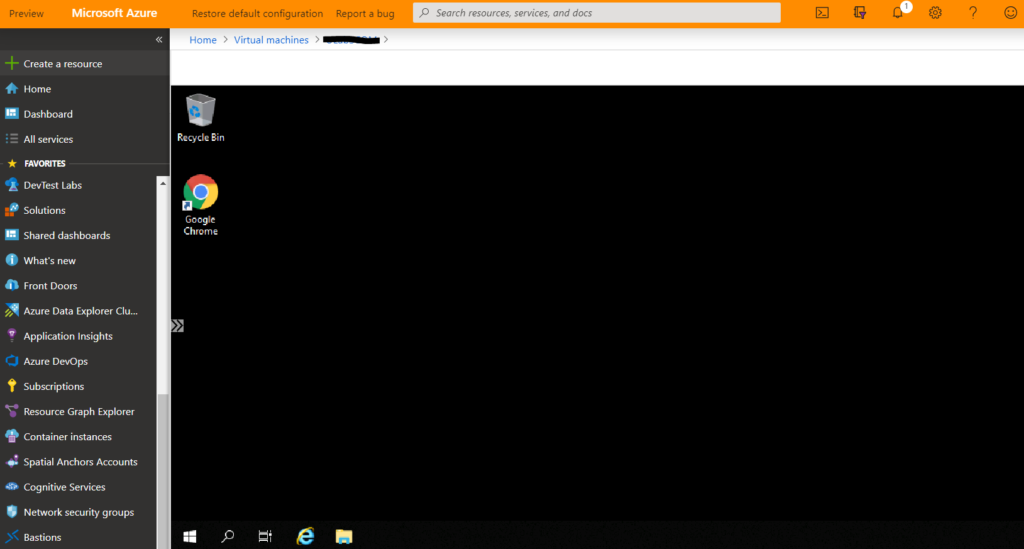
And there you have it, your VM is securely accessible through the Azure Portal without needing a public facing IP address.
Conclusion
Bastion is a fantastic and a much needed service which allows secure access to your cloud Windows and Linux VMs without any exposure of public IPs ultimately allowing the removal of the VM attack surface in your Azure environment.
![]()
